

The Secure Internet Access Gateway is a highly available, egress filtering proxy and NAT gateway. The gateway restricts HTTP and HTTPS egress traffic from VPC resources to a whitelisted set of hostnames (FQDN). This solution is effective where traditional IP-based firewalls fall short. Access to package repositories and AWS APIs can be provided to instances in private subnets without granting them broad internet access. The gateway is ideally suited to protect your EC2 instances, AWS Workspaces and even Lambda functions from harmful internet traffic while still providing access to update servers, specific websites and services.
The gateway can operate in explicit and transparent mode. In explicit mode, the instance needs to be provided with the gateway's proxy address. The explicit mode provides more granular control over what application has access to the internet. In transparent mode the gateway is added to the subnet's route table allowing traffic to be filtered on its way out to the internet. No changes to applications on EC2 instances are necessary. The transparent mode is useful in scenarios where an application does not provide an option to define a proxy.
The Secure Internet Access Gateway is powered by the AWS Network Load Balancer (NLB). The gateway can therefore easily be shared with other VPCs in the same region using the VPC PrivateLink feature. Please note that only explicit mode is available when using PrivateLink (see https://docs.aws.amazon.com/console/vpc/endpoints/endpoint-service).
HIGH AVAILABILITY The gateway can easily be deployed in multiple availability zones for redundancy.
TRANSPARENT PROXY Optionally filters traffic in transit without explicit proxy configuration.
FILTER BY HOSTNAME Control egress traffic by destination hostname instead of IP address.
This solution is best deployed through CloudFormation templates. CloudFormation is an Infrastructure as Code (IaC) service provided by AWS which makes the set up of complex cloud infrastructures fast and reliable.
We are offering two templates. We highly recommend to get started with the New VPC Template if you are unfamiliar with CloudFormation or want to simply test out the solution. The Existing VPC Template is the best choice if you already have a VPC in place and want to enable the Secure Internet Access Gateway for your VPC.

This template will create a VPC from scratch and will deploy the Secure Internet Access Gateway load-balanced across two availability zones. EC2 instances launched in the private subnet will automatically use the gateway for any egress traffic. This is the preferred setup and fastest way to get started.
Using the PrivateLink feature you can easily share this gateway with other VPCs in the same region. Please refer to the AWS documentation on how to enable PrivateLink for the Network Load Balancer.
This template deploys the Secure Internet Access Gateway into an existing VPC in your AWS account. Please ensure that your existing VPC fulfills the following requirements:
If your VPC does not fullfill these requirements please contact us and we will customize the template to fit your needs.
The Whitelisted Domains parameter defines the domain names that can be accessed through the gateway. All other requests will be blocked and return a 403 HTTP error code. If the connection was tried over an encrypted connection, the connection will simply be dropped. Hostnames can be defined to include all subdomains by prefixing them with a dot. For instance, .amazonaws.com will whitelist amazonaws.com and all of its subdomains. Be careful to not specify domain names too broadly. .amazonaws.com will also include access to any S3 bucket which might not be desired.
This chapter is only applicable if you run the proxy in explicit mode.
The CloudFormation template will output the hostname of the Network Load Balancer (NLB) under Outputs, ProxyAddress. The port for the HTTP proxy is always 3128. On most Linux systems it is sufficient to set the http_proxy and https_proxy environmental variables. The majority of client applications will pick up these variables and configure themselves accordingly.
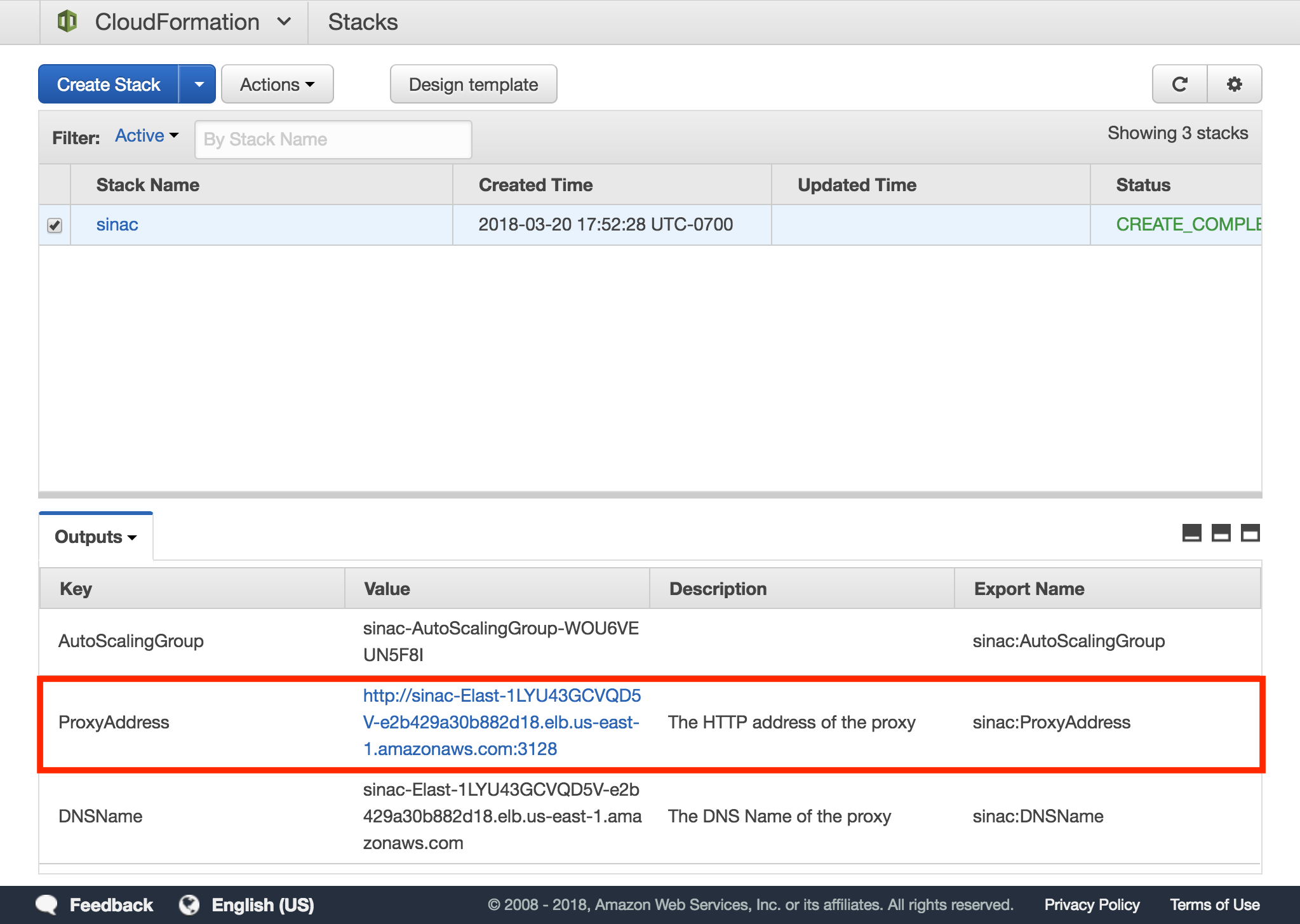
We are using http://elb-abd7a4647.elb.us-east-1.amazonaws.com:3128 as an example in the following configurations. Make sure to replace it with your load balancer's address from the Outputs tab.
For Ubuntu, Debian, CentOS, Amazon Linux systems
To set the proxy configuration system wide, open the file /etc/environment and add the following lines. You will need to log out and back in again for the changes to take effect.
http_proxy=http://elb-abd7a4647.elb.us-east-1.amazonaws.com:3128
https_proxy=http://elb-abd7a4647.elb.us-east-1.amazonaws.com:3128
To set the proxy only for the active session, execute the following statements in a shell session:
export http_proxy=http://elb-abd7a4647.elb.us-east-1.amazonaws.com:3128
export https_proxy=http://elb-abd7a4647.elb.us-east-1.amazonaws.com:3128
For applications using the Java Virtual Machine
In most cases, it it sufficient to execute enable the JVM flags when starting your JVM on the command line:
JAVA_FLAGS="-Dhttp.proxyHost=elb-abd7a4647.elb.us-east-1.amazonaws.com -Dhttp.proxyPort=3128"
java ${JAVA_FLAGS} ...
If you want to exclude requests to local hosts from being forced through the proxy, you can define a list of exceptions like this:
JAVA_FLAGS=$JAVA_FLAGS' -Dhttp.nonProxyHosts="localhost|127.0.0.1|10.*.*.*"'
For more details, see https://docs.oracle.com/javase/8/docs/technotes/guides/net/proxies.html.
Access logs are written to AWS CloudWatch Logs in the /netcubed/sinac/... log group. Logs are retained for 7 days by default. You can access the log files through the AWS console. The format is defined as
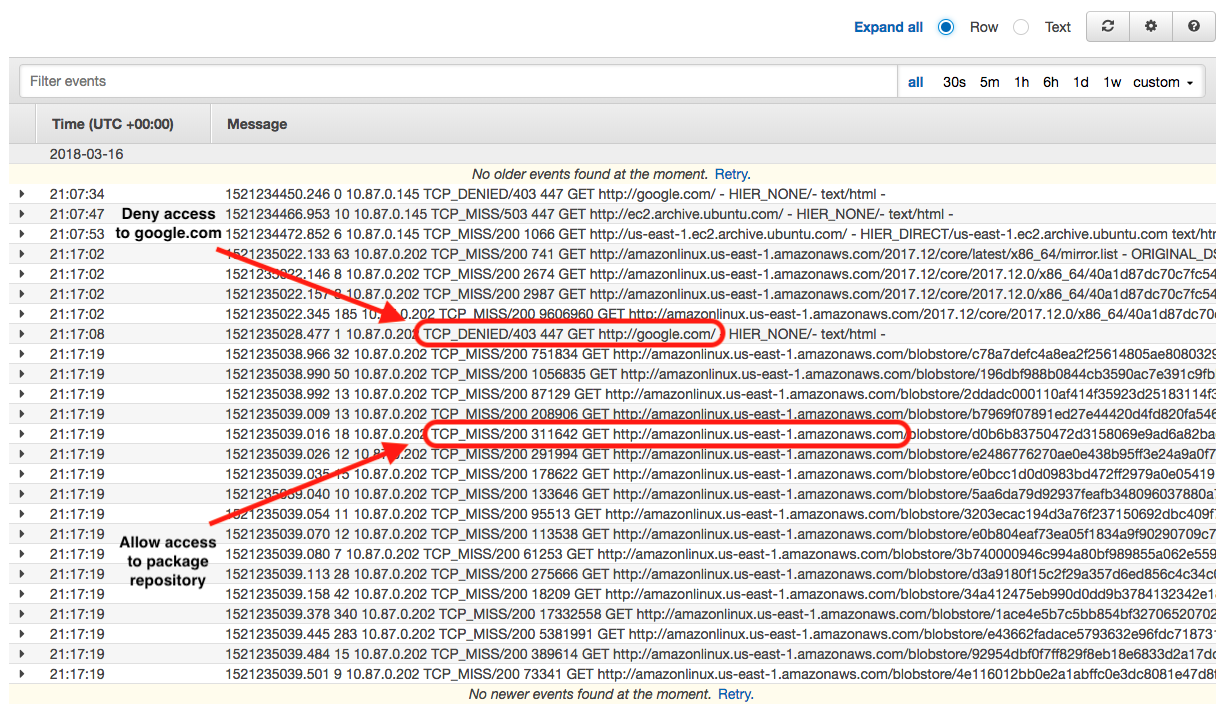
Additionally, the service creates a new metric that counts the number of requests with an Access Denied response. You can manually create alarms that alert you if the number of denied requests reaches a certain threshold.
The server can be patched manually by accessing the server via SSH. The SSH port is only accessible from IPs within the VPC. Execute sudo yum update -y to upgrade the operating system. Reboot the instance after updated packages have been installed.
We will also be publishing new AMIs after critical security vulnerabilities have been published. As a subscriber to the AMI you will be notified immediately.
You can at any time update the Whitelisted Domains parameter in your CloudFormation stack. The gateway will check for changes of the Whitelisted Domains parameter every 60 seconds. Changes will therefore be reflected almost instantly.
The following hostnames have been proven sufficient to provide access to the Microsoft update servers.
.update.microsoft.com,.download.windowsupdate.com,.ctldl.windowsupdate.com
The explicit mode requires your application to be aware of the proxy. This is usually accomplished by setting the http_proxy and https_proxy environmental variables to the hostname of the Network Load Balancer (port 3128). The explicit mode is recommended because it allows you to define which applications are able to connect through the proxy to the internet. If the proxy configuration is not provided to an application, any internet connections will simply fail. In cases where the application can not be configured to use a proxy, we recommend the transparent mode.
In transparent mode the routing tables of the VPC are configured to route internet traffic from private subnets through the Secure Internet Access Gateway instances instead of routing internet traffic directly to the VPC's Internet Gateway. This has the benefit that the application on your EC2 instances won't need to be made aware of the proxy. Internet connectivity will simply work as long as the EC2 instance is connecting to a whitelisted domain.
A public subnet is attached to a route table that has a route to an internet gateway (usually the 0.0.0.0/0 route). This provides all instances in the public subnet with transparent internet access. The instances will also need to have a public IP attached to them in order to access the internet.
A private subnet, on the other hand, does not have a route to an internet gateway and usually does not provide public IPs to the instances in the subnet. Even if an instance in a private subnet was launched with a public IP, internet access would not be possible. Security best practices and regulations in some industries require servers to be located in a private network segment which private subnets can provide.
The proxy will return an HTTP response with status code 403 to the client if the destination hostname is not whitelisted. The response body include the phrase ERR_ACCESS_DENIED. The full response including all headers can be seen in the following curl request.
$ curl --include google.com
HTTP/1.1 403 Forbidden
Server: squid/3.5.27
Mime-Version: 1.0
Date: Wed, 21 Mar 2018 01:00:20 GMT
Content-Type: text/html;charset=utf-8
Content-Length: 18
X-Squid-Error: ERR_ACCESS_DENIED 0
Vary: Accept-Language
Content-Language: en
X-Cache: MISS from ip-10-87-0-78.ec2.internal
X-Cache-Lookup: NONE from ip-10-87-0-78.ec2.internal:3128
Via: 1.1 ip-10-87-0-78.ec2.internal (squid/3.5.27)
Connection: keep-alive
ERR_ACCESS_DENIED
v1.1.0